Cyber resilience entails an organization’s capability to proactively prepare for, effectively respond to, and swiftly recover from a wide range of cyber threats. Resilient organizations adeptly navigate anticipated and unforeseen challenges, thus preempting potential pitfalls stemming from unpreparedness.
In 2022, the average time to discover and mitigate a breach was 277 days, roughly equivalent to nine months. (Stats: IBM)
In this context, maximizing cyber resilience with Security Information and Event Management (SIEM) becomes an efficient approach. By integrating and analyzing diverse data sources, SIEM enables real-time detection and response to security incidents. SIEM offers advanced analytics and threat intelligence integration, enhancing the ability to pinpoint and neutralize threats. In this article, we’ll explore how to leverage SIEM to bolster your cyber resilience strategies.
How do you ensure cyber resilience?
To ensure cyber resilience, it’s imperative to acknowledge the challenges posed by evolving networks and the expanding threat landscape. As evident, enterprises often grapple with limited real-time visibility of their IT assets’ security posture. They face uncertainties regarding what needs protection, potential breach points, and the efficacy of existing security measures.
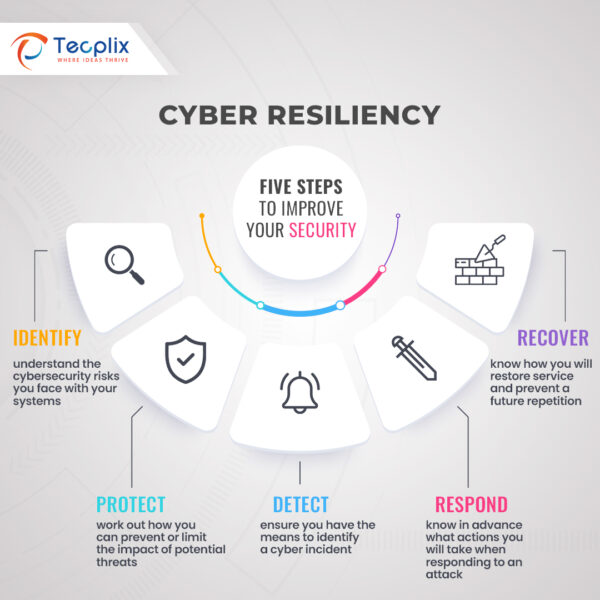
Image 1: Steps to Improve Cyber Resilience
However, a comprehensive cyber resiliency strategy encompassing proactive measures, detection capabilities, effective response, governance, and adaptability can help. Proactive protection entails crucial components like robust asset management, encryption, access controls, security policies, and malware protection. While detection relies on tools such as Endpoint Detection and Response (EDR), Intrusion Detection Systems (IDS), and Network Detection and Response (NDR) to identify potential threats promptly.
In the event of a cyber incident, a resilient organization must have measures in place for business continuity and recovery. This includes continuity management, incident response, and information-sharing protocols. Effective governance ensures that processes and technologies function optimally within the cyber resilience program. This involves commitments from the board, certifications, internal audits, and risk management. The dynamic nature of cyber threats necessitates adaptability in the resilience strategy.
The importance and benefits of SIEM
SIEM provides important reporting features that can assist enterprises in meeting regulatory obligations and demonstrating their security posture to stakeholders. Compliance regulations such as HIPAA, PCI-DSS, and GDPR mandate businesses to implement security protocols for safeguarding sensitive information. Moreover, SIEM systems aid enterprises in detecting and addressing potential insider threats. Additionally, it can help identify suspicious user activity and detect potential insider threats, enabling security teams to take proactive measures to prevent data breaches.
- Centralized security management: SIEM allows security teams to identify and respond to security incidents from a single location.
- Proactive threat detection: Through real-time analysis of security events, SIEM systems identify patterns and anomalies that indicate a potential threat.
- Compliance: SIEM systems provide reporting capabilities that can help organizations meet compliance requirements. It generates reports that demonstrate an organization’s security posture, and help meet regulatory requirements.
- Cost-effective: SIEM operates at reduced cost and minimizes the need for expensive security hardware and software.
How does a SIEM work?
SIEM offers proactive threat detection capabilities for enterprises of all sizes. Its effectiveness lies in its structured approach, which encompasses continuous monitoring, in-depth analysis, and timely reporting of potential security risks. This ensures that any suspicious activities or threats are identified and addressed swiftly, enhancing the overall security posture of the enterprise.
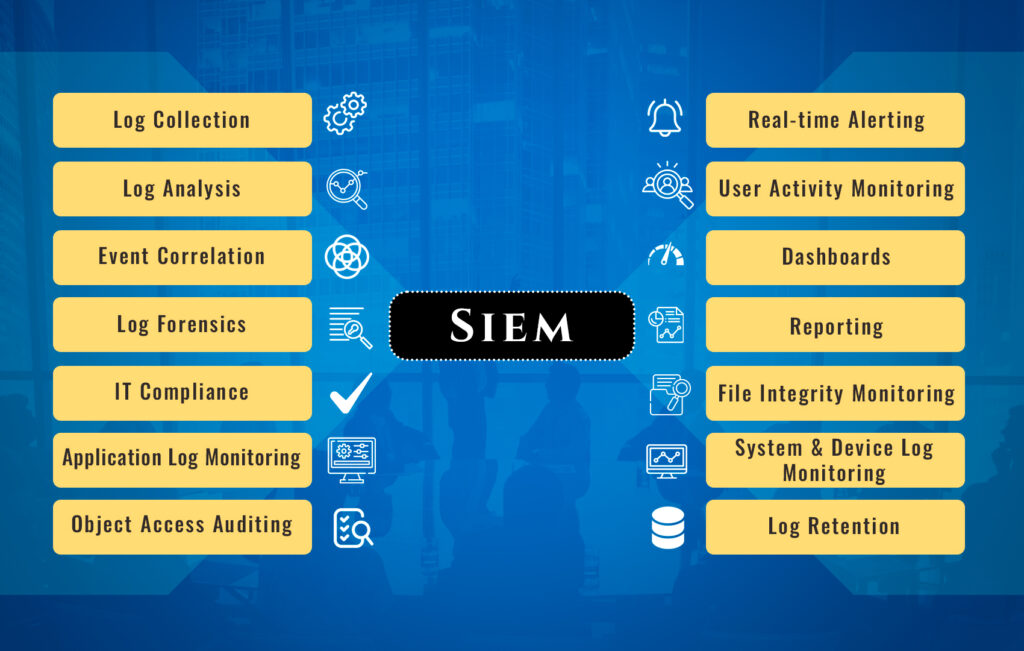
Image 2: SIEM Functionality
- Collection: SIEM captures security events from a variety of sources, including firewalls, servers, and apps. It evaluates the gathered data to identify potential security concerns.
- Correlation: After data collection, SIEM systems correlate the events to identify patterns and anomalies. For example, an SIEM system might correlate login attempts from a specific IP address with a failed attempt to access a server.
- Alerting: If the SIEM system detects a potential security threat, it generates an alert to notify security teams. The alert contains information about the security event and guides how to respond.
- Investigation: Security teams determine whether the threats are legitimate or not. Additionally, security tools like intrusion detection systems may be employed, to gather more information.
- Response: Security teams take over once a threat is verified. They will contain the threat by blocking access to compromised systems, resetting passwords, or applying software patches to mitigate the threat.
- Reporting: With robust reporting functionalities, SIEM empowers security teams to scrutinize security incidents and discern patterns.
Implementing your Use Cases
To harness the power of a SIEM solution, you must create a set of well-defined use cases that outline the security threats you aim to tackle and the outcomes you wish to achieve. Begin with the highest priority and follow these steps to implement them.
Step 1. Define requirements and scope
When defining requirements and scoping the SIEM, address the following:
- Identify critical IT assets for protection.
- Assess prevalent threats and their potential impact.
- Consider business, compliance, and security priorities.
Step 2. Select data sources and integrate them into your SIEM
Determine which logs and data sources are vital for detecting threats related to the use case. Evaluate characteristics like location, verbosity, size, data type, data points, and rotation frequency. Additionally, document application details such as name, version, and operating system. Refer to vendor documentation for data assimilation and log file generation. Integrate chosen data sources with your SIEM and ensure seamless communication.
Step 3. Formulate rules for your use case
SIEM correlation rules dictate how the solution aggregates and analyzes various types of data. They define specific events to flag, such as cyberattack attempts, compliance breaches, or privilege escalations. For instance, you might set a rule to alert on multiple failed login attempts within a specific timeframe. Advanced analytics may include pattern matching and machine learning.
Craft rules and establish baselines and thresholds based on in-depth knowledge of your IT environment, threat landscape, and attacker tactics. Given evolving tactics, continuously develop new correlation rules.
Start by leveraging the SIEM’s built-in rules, comprehending them fully, and then adapt as needed. As you gain experience, begin crafting your own rules.
Step 4. Test and fine-tune
Initial implementation may yield false positives or overlook genuine threats. For example, the SIEM might mistake a legitimate vulnerability scan for an aggressive attack, generating a stream of alerts. Additionally, check for false negatives, where true threats go undetected.
Thoroughly test each use case and adjust rules and thresholds until the desired behavior is achieved. Aim to minimize false positives while not missing true threats.
Step 5. Monitor performance
Continuously assess results to ensure the SIEM functions as expected. Given the rapidly changing threat landscape, ongoing monitoring supports use case maintenance and the development of new ones to address emerging threats.
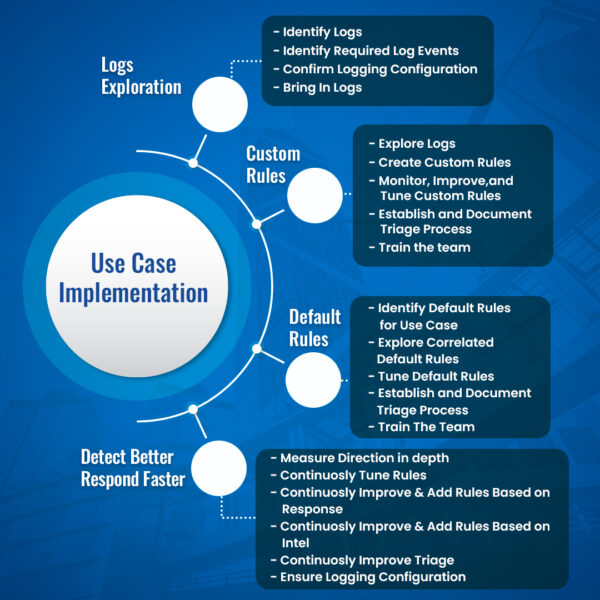
Image 3: SIEM Use Case Implementation
Tuning Your SIEM Correlation Rules
Common issues impacting correlation rules include:
- Disabled rules that should be enabled, potentially causing the oversight of legitimate threats.
- Lack of customization for out-of-box rules, necessitating adaptation for tailored alerts and reports.
- Insufficient filtering leads to overwhelming log volume; consider sending only relevant data to the SIEM.
- Inadequate rule maintenance, as rules need updates, especially with new data sources.
- New rules potentially conflict with existing processes, warranting consideration of overall logic.
Tuning Your SIEM Alerts
Strive for precise alerts that highlight security events without overwhelming or missing genuine threats. Assess behavioral baselines and rule-encoded unusual behavior. Confirm all relevant events trigger SIEM alerts and ensure notifications reach the appropriate teams.
Also, track new systems and applications to bolster on-prem and cloud security.
Best practices for SIEM implementation
To maximize SIEM value, adhere to these best practices:
- Establish clear goals based on the threat landscape and business, compliance, and security objectives.
- Designate a dedicated SIEM administrator for proper upkeep.
- Begin with out-of-box rules, customizing them as you become more familiar with the system. Gradually develop your own rules.
- Thoroughly test and fine-tune.
Elevating cyber resilience with SIEM capabilities
Tecplix streamlines your cyber resilience journey with a fusion of unparalleled expertise, extensive experience in SIEM implementation, and continuous knowledge transfer with partners, coupled with our dedication to pushing the boundaries of innovation for truly customized and impactful solutions.
- Precise Data Identification: We pinpoint the critical data that demands safeguarding, ensuring nothing falls through the cracks.
- Proactive Security Controls: Tecplix is your proactive sentinel, identifying and swiftly closing security control gaps before they can be exploited.
- Alert Prioritization, not Fatigue: We believe in actionable alerts, ensuring that true threats are identified swiftly without drowning your team in false positives.
- Contextualized Incident Response: When an incident occurs, time is of the essence. Tecplix equips your team with the contextual information they need to respond swiftly and decisively.
- Rapid Recovery and Asset Prioritization: We understand that in the wake of an incident, swift restoration is paramount. Our approach ensures that critical assets take precedence.
What Sets Us Apart?
- Unparalleled Expertise: We boast an unrivaled mastery of leading SIEM & SOAR architectures and their seamless integration.
- Proven Track Record: With hundreds of cybersecurity projects completed, our results speak for themselves.
- Certified Consultants: Our team is composed of seasoned, certified consultants, each possessing a wealth of experience.
- Technical Prowess: We possess deep technical proficiency in networking devices, operating systems, software and device audits, logging, and security subsystems.
- End-to-End Lifecycle Experience: Our consultants bring considerable hands-on experience across the entire security solutions lifecycle.
Tecplix not only strengthens your defensive capabilities but also empowers you to maintain continuous resilience and adaptability in the face of unforeseen challenges. We provide comprehensive support from project initiation to completion and offer ongoing assistance as needed.
Read a related blog here:


