Technological advancements have drastically reshaped the business landscape, offering expanded market access, improved consumer engagement, and heightened service delivery. Despite these advancements, a fresh spectrum of destructive, ever-changing, and imperceptible risks has emerged.
According to Verizon, 61% of all security breaches involved credential thefts acquired through social engineering methods or hacked using brute force tactics.
Another study reveals that 44% of security experts believe implementing an Identity and Access Management (IAM) solution can address their current security vulnerabilities.
In this context, IAM acts as a reliable defense by identifying users and tailoring their access to resources based on roles and responsibilities. This ensures that sensitive data remains within authorized confines, thereby, minimizing the peril of breaches, unauthorized entry, and compliance while fortifying security.
What Is IAM?
IAM incorporates management of the entire lifecycle of user identities and access across all enterprise resources, whether in data centers or the cloud. The identity manager regulates access and entitlements through defined roles, policies, and tools, extending privileges to network entities (users and devices) for diverse applications, both on-premises and in the cloud.
IAM’s objective is to grant a single digital identity for each individual or item. Where, users encompass customers, partners, and employees, while devices span computers, smartphones, routers, servers, controllers, and sensors. Once established, the digital identity is maintained, modified, and monitored throughout each user’s or device’s access lifecycle.
Identity Management in Practice
In a broader sense, identity management facilitates access to enterprise assets, aligning with user and device entitlements within specific contexts. This encompasses onboarding users and systems, authorizing permissions, and timely offboarding of users and devices.
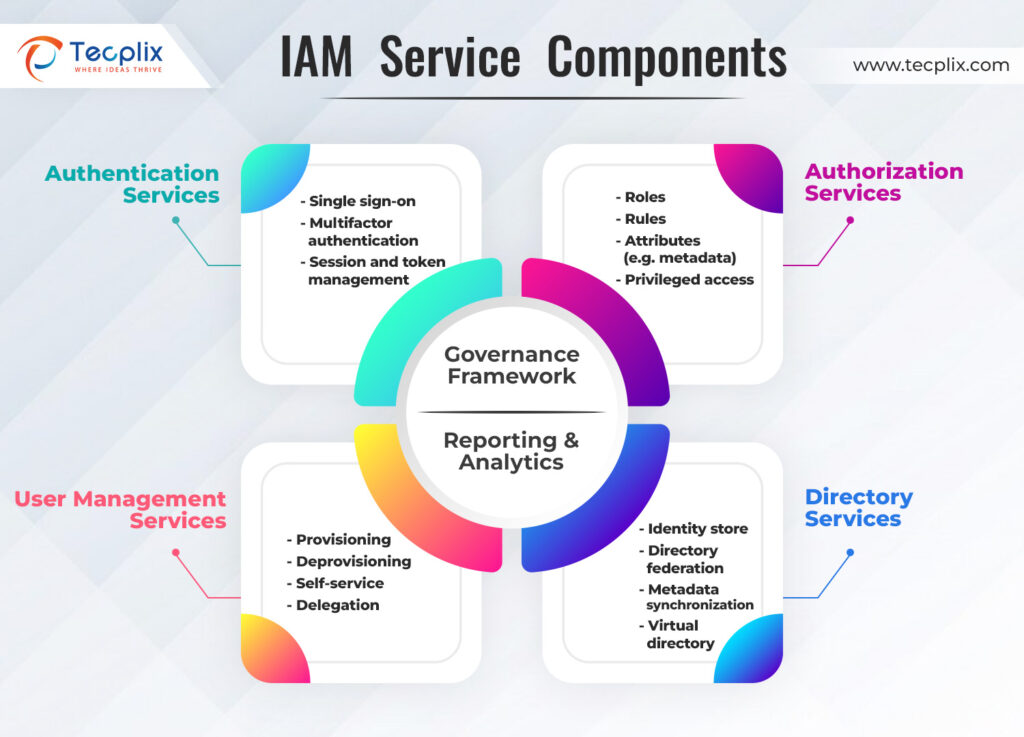
Figure1: IAM Service Components
Key Components of an IAM Framework
User Management
- Establishing and configuring user roles within the organization
- Defining the specific permissions and access levels for each user or group within the system
- Applying the relevant roles for new employees upon joining the company
- Ensuring timely and appropriate role changes when employees transition to different positions or departments
- Deleting or modifying roles when an employee exits the company, ensuring no residual access remains
Authentication
- Verifying the identity of users accessing the system
- Implementing Multi-factor authentication (MFA)
- Implementing biometric or token-based authentication
- Continuously updating authentication methods to combat evolving security threats and vulnerabilities
Authorization
- Governing the access privileges granted to the users
- Role-Based Access Control (RBAC) to assign specific permissions based on predefined roles
- Attribute-Based Access Control (ABAC) to adjust access based on contextual and environmental factors
- Strict business policies to ensure that only authorized individuals access critical assets under appropriate circumstances
Centralized User Database
- A centralized source for user information and configurations
- Single Sign-On (SSO) by storing user data required for seamless authentication across multiple platforms
- Interoperability with diverse identity systems to streamline user management and access control
- Housing all user-related data in a centralized and easily accessible location
Monitoring and Audit
- Tracking password resets and modifications
- Identifying and managing orphan accounts
- Monitoring privileged account activities
- Tracking the number and types of roles associated with each user or account
- Detecting and addressing separation of duties (SoD) violations
- Monitoring non-human identities (service accounts)
Benefits of IAM
The role of IAM extends beyond simplifying identity, access, or authorization in organizations. It offers several benefits that can help streamline processes and secure critical assets:
Enhanced Security
- Uniform security policies applied across the enterprise
- Network Access Control (NAC) solution tools restrict resource access for specific users
- Reduced unauthorized access to sensitive data
Stronger Compliance
- Aides in compliance mandates such as HIPAA, NIST, PCI DSS, and others
- IAM methods like SSO, MFA, RBAC, and “least privileges” help meet regulatory requirements
- Easy controls and centralized management offer better agility against changing business needs
Higher Employee Productivity
- Security measures like SSO and MFA streamline access management
- IAM enables automated user provisioning, facilitating resource access without IT bottlenecks
Reduced IT Costs
- Task automation in identity and authorization management
- Cloud-based IAM services reduce on-premises infrastructure expenses
- IAM significantly enhances security, compliance, productivity, and cost-efficiency for businesses
Neglecting IAM can Expose to Unprecedented Risks
Excessive Permissions
- Assigning unnecessary permissions to identities disrupts their intended functions
Least Privilege policies prevent broad permissions, favoring specific roles only. Through refinement and delegation of permissions into multiple roles, excessive access can be curbed.
Misconfigurations
- Unauthorized logins, open APIs, and MFA lapses expose systems
- Misconfigurations are a top cause of breaches
Cloud Security Posture Management tools detect and rectify these vulnerabilities.
Compliance and Audit Challenges
- Regulations like HIPAA, PCI DSS, and others demand stringent data security
IAM tools ensure proper data access management and prevent breaches. Precise IAM tools aid in audits by detailing identities and their access.
Privilege Escalation
- Poor privilege control allows attackers to elevate their access from low-level identities to high
Accurate insights into identities’ abilities, their permissions, and effective detection tools can curb such risks.
Multi-cloud Risks
- Managing identities across multiple clouds is complex
- Cross-cloud accesses are not easily detectable and pose a serious threat
Advanced IAM tools are designed to prevent such risks.
Insider Threats and Privilege Abuse
- Highly privileged identities entice attackers
- Preventing intentional and unintentional privilege abuse limits internal risks
Refined privilege allocation curtails lateral movement by delegating permissions by roles with very fine-tuned privileges.
Poor Access Management Policies and Practices
- Manual security protocols without a clear process, may lead to granting greater access than required
Automation streamlines identity management, addressing security gaps, while intelligent workflows operationalize identity programs effectively.
Data Access Risks
- Insufficient identity management directly impacts data security
- Breaches lead to disruptions, fines, and customer trust issues
Off-boarding Employees/Orphaned Identities
- Proper offboarding limits future threats
- Cloud-native identity visibility ensures thorough offboarding
Implementing IAM
Identity and Access Management (IAM) has evolved into a critical aspect of modern cybersecurity strategy for organizations. To maximize security benefits, companies are implementing IAM tools and processes. Implementing robust identity and access management requires a comprehensive understanding of the network resources, server architecture, and critical resources. A methodical approach incorporating best practices and the right tools is the way toward robust IAM.
Best Practices for IAM Implementation:
Embrace a Zero Trust Approach to Security
Implicit trust in applications and tools can jeopardize security. Adopting a zero-trust model ensures constant user verification before granting access to company resources.
- Implement Zero Trust principles: never trust, always verify; assume breach; and least-privileged access.
- Synergize IAM tools with Zero Trust architecture for rigorous user authentication, reducing risks of unauthorized access.
Identify and Safeguard High-Value Data
Securing crucial data starts with limiting access. Recognize high-value assets, assess where they’re stored, and apply access control policies to ensure data security.
- Identify sensitive data like trade secrets or personal information.
- Utilize Azure, GCP, and AWS IAM practices to safeguard cloud-stored data.
Enforce a Robust Password Policy
Strong passwords and unique authentication are vital. Regularly review password strength and employ Multi-Factor Authentication (MFA) for added security layers.
- Ensure complex, unique passwords for each user.
- Implement enhanced password protocols.
Implement Multi-Factor Authentication (MFA)
Validating a user’s identity is crucial. MFA tools provide multiple validation steps, ensuring authorized access.
- Utilize biometric, possession, and knowledge authentication methods.
- Enhance security with layered authentication.
Automate Workflows
IAM tools facilitate automation for enhanced security, reducing manual errors, and aiding compliance needs.
- Automate tasks like account creation and access provisioning.
- Simplify compliance reporting through automated logs.
Embrace the Least Privilege Principle
Limit access as much as possible without impeding workflows, employing role-based and attribute-based access controls.
- Define minimum privilege levels for each role.
- Regularly audit and reduce unnecessary permissions.
Implement Just-in-Time Access
For temporarily elevated privileges, employ just-in-time access, ensuring granular and controlled access.
- Temporarily elevate permissions without compromising security.
- Ideal for external users requiring periodic access.
Utilize RBAC and ABAC Policies
Combine role-based and attribute-based access controls for efficient user management.
- Define access based on roles and attributes for streamlined provisioning.
- Automate access changes as users transition roles.
Regularly Audit Resource Access
Continuously track access needs and remove unnecessary permissions to maintain security.
- Conduct regular audits to prevent over-provisioning.
- Create an auditing schedule to prioritize security.
Centralize Log Collection
Store logs centrally, preferably in the cloud, ensuring accessibility and compliance without compromising security.
- Stream audit logs to cloud storage or SIEM/SOAR tools for better insights.
- Ensure secure log storage in compliance with cloud IAM practices.
Employ IAM Solutions Compatible with Existing Tools
Choose IAM solutions that seamlessly integrate with your current tech stack, reducing the need for extensive reconfigurations.
- Prioritize solutions that support existing tools.
- Define user account management policies in advance for smoother integration.
By adopting these IAM best practices, organizations can fortify their security posture while aligning with evolving IAM strategies.
Simplified and Streamlined IAM
In today’s dynamic digital landscape, securing your organization’s critical data and systems is paramount. A robust Identity and Access Management (IAM) solution stands as the cornerstone of a secure digital infrastructure. Tecplix offers tailored solutions to safeguard your digital assets and empower your workforce.
Our approach commences with thorough consultations, where our seasoned experts collaborate closely with clients to grasp their unique needs, challenges, and long-term goals. This collaborative effort serves as the foundation for a comprehensive implementation roadmap. As we immerse ourselves in the deployment intricacies, our aim remains a seamless transition that minimizes disruptions and maximizes operational efficiency.
We continuously adapt and optimize these solutions to align with the evolving demands of organizations. Our commitment resides in refining and fine-tuning IAM frameworks to future-proof your security architecture.
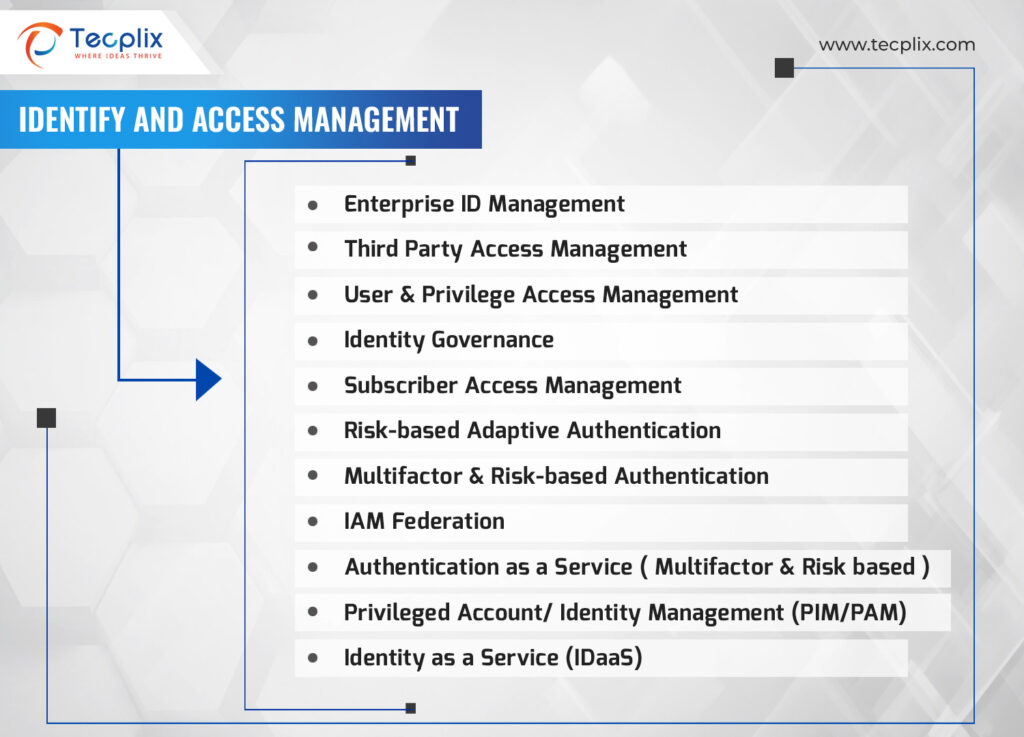
Figure 2: Tecplix IAM Services
- Enhanced Security: Safeguard your sensitive data and systems against unauthorized access, significantly reducing the risk of data breaches and cyber threats.
- Improved Compliance: Ensure strict adherence to data privacy regulations and industry standards, effectively mitigating the possibility of legal and financial penalties.
- Streamlined Access Management: Simplify user access protocols, diminishing administrative overheads and allowing IT resources to focus on strategic initiatives.
- Empowered Workforce: Grant your employees secure access to essential resources, enabling them to perform their roles effectively, thus amplifying productivity and satisfaction levels.


