In today’s ever-evolving digital landscape, the proliferation of threats and increasing complexity necessitate a more intelligent and adaptable approach. Organizations need a collaborative and efficient security system with complete visibility across all security operations. While having the right tools and systems in place is crucial, the expertise to harness their full potential is essential. The priority is seamlessly integrating various security components for precise threat prevention, detection, and response.
Between March 2022 and March 2023, data breaches globally cost companies an average of 4.45 million U.S. dollars. (Source: Statista)
Every organization holds a broad spectrum of valuable assets encompassing intellectual property, sensitive personnel data, critical business systems, essential infrastructure, brand reputation, and more. Given the potential severity of security incidents, organizations struggle to enhance their security posture. In order to ensure security, they need robust monitoring and defense mechanisms. These mechanisms should swiftly identify threats and raise the alarm when any unusual or suspicious activities occur.
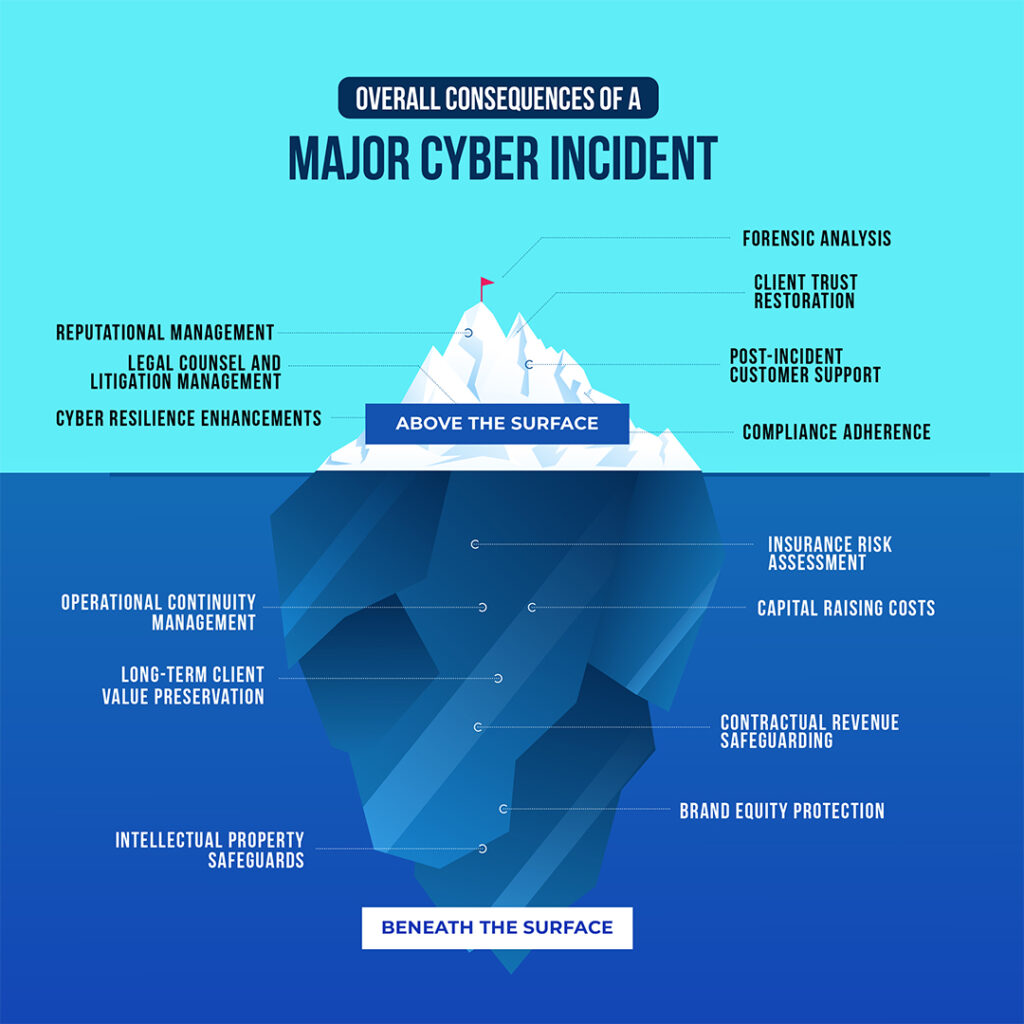
Consequences of a Cyber Incident
Proactive Detection & Prevention with Managed SOC
The core mission of a Security Operations Center (SOC) revolves around the vital role of security monitoring and alerting. This encompasses the meticulous collection and scrutiny of data to uncover suspicious activities and enhance an organization’s security posture. The SOC garners threat data from a variety of sources, such as firewalls, intrusion detection systems, intrusion prevention systems, security information and event management (SIEM) platforms, and threat intelligence feeds. When the system detects anomalies, irregular trends, or indicators of compromise, it promptly dispatches alerts to SOC team members.

Components of Security Operations Center (SOC)
What Does a SOC’s Function Encompass?
- Discovery of Assets: The SOC maintains a comprehensive inventory of all hardware, software, tools, and technologies employed within the organization. This enables the continuous monitoring of assets for potential security incidents.
- Behavioral Monitoring: Operating around the clock, the SOC diligently scrutinizes the organization’s technological infrastructure to identify any aberrations. The organization swiftly detects and addresses irregular activities using both reactive and proactive measures, while minimizing false positives through behavioral monitoring.
- Activity Logging: Every interaction and communication occurring across the enterprise is meticulously logged by the SOC team. These activity logs serve as a valuable resource for backtracking and identifying past actions that might have led to a cybersecurity breach. Moreover, log management aids in establishing a baseline for what constitutes normal activity.
- Alert Prioritization: Recognizing that not all security incidents are of equal significance, the SOC assigns severity rankings to alerts. This allows the SOC team to focus on addressing the most critical threats first.
- Incident Response: SOC teams swing into action when a security compromise is detected, launching a swift and coordinated response to mitigate the threat.
- Root Cause Investigation: After an incident, the SOC often takes on the responsibility of investigating the who, what, when, and why behind the breach. This process relies on log data to trace the root cause and prevent future occurrences.
- Compliance Management: SOC team members operate in alignment with organizational policies, industry standards, and regulatory requirements.
What Are the Advantages of Having a Managed SOC?
A well-implemented SOC delivers a plethora of benefits, which include:
- Continuous Monitoring and Analysis: The SOC ensures ongoing scrutiny of system activity, offering real-time insights into potential security threats.
- Enhanced Incident Response: With a SOC in place, the response time between the occurrence of a security breach and its detection is drastically reduced.
- Reduced Downtime: Quick identification and response to security incidents minimize the potential downtime and disruptions to operations.
- Centralized Asset Management: A SOC streamlines the management of hardware and software assets, allowing for a more comprehensive and real-time approach to infrastructure security.
- Efficient Collaboration and Communication: Effective communication and coordination within the SOC team enhance the overall response to security incidents.
- Cost Reduction: The presence of SOC leads to decrease in both direct and indirect costs associated with managing cybersecurity incidents.
- Enhanced Trust: Organizations gain the trust of employees and customers when they see a strong cybersecurity posture.
- Control and Transparency: The SOC provides a clear chain of control over systems and data.
Elevating Your Cybersecurity Experience
When it comes to keeping your digital assets safe, Tecplix’s Managed Security Operations Center (SOC) services have got your back in the most agile and effective way. Our method is all about understanding your unique digital environment and making sure it stays secure. Tecplix gives you swift and clear-cut insights, so you know exactly what’s happening. Plus, we’ve got a watchful team on duty 24/7, making sure your digital world stays trouble-free. We don’t just point out issues; we fix them, making your digital space safer.
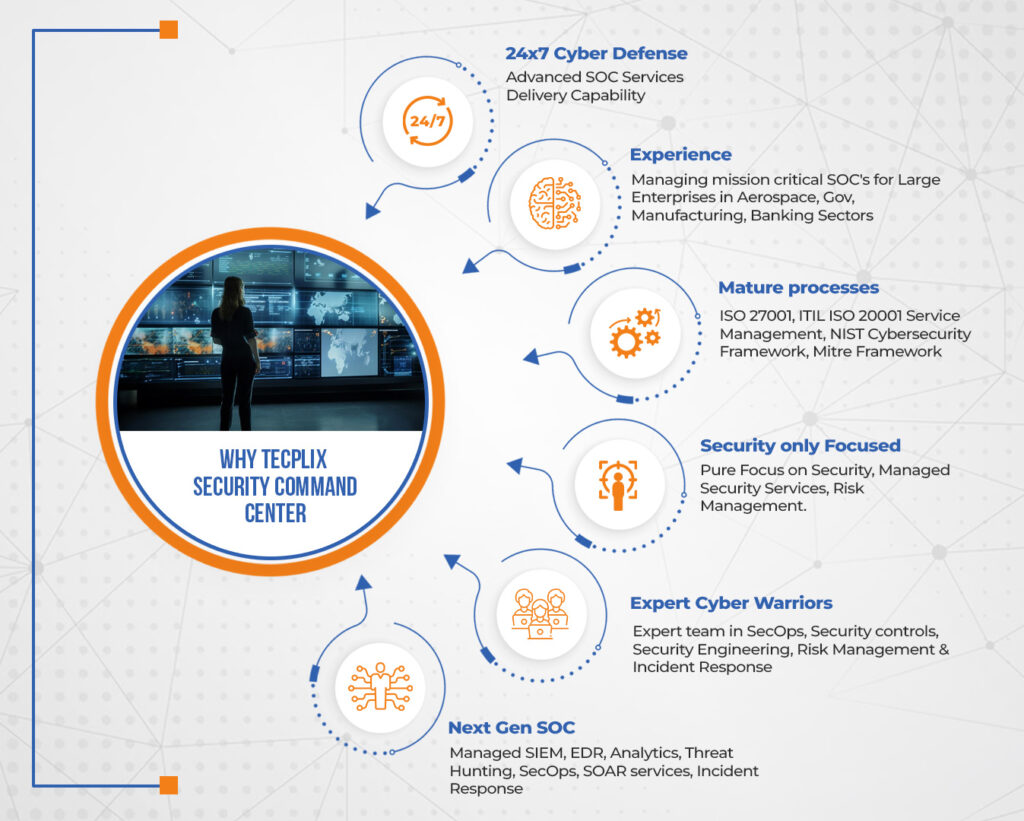
Tecplix Security Command Center
Tecplix offers advanced cybersecurity solutions designed with your needs in mind:
- Expert SOC Resources: Our seasoned team of cybersecurity professionals brings extensive experience to safeguard your digital infrastructure.
- Real-time Threat Intelligence: Stay ahead of evolving threats with dynamic updates, enabling proactive measures against potential risks.
- Proactive Threat Hunting: Our experts actively seek out potential dangers, ensuring swift identification and mitigation of risks.
- Swift Incident Response: Count on Tecplix for decisive and rapid response, minimizing any potential impact on your operations.
- Customized Security Solutions: Tailored to fit your unique organizational needs, providing precise levels of protection.
- Comprehensive Endpoint Protection: Extend your defense strategy to cover all endpoints, ensuring a thorough shield against evolving threats.
- OT/ICS Security Expertise: Specialized in safeguarding critical operational technology and industrial control systems.
- Continuous Monitoring and Alerting: Receive prompt notifications of validated threats, allowing for timely action.
- Platform Optimization: Leave platform design, implementation, and configuration management to us for peak performance.
- Use Case Management: Fine-tuned threat detection rules, digital playbooks, and seamless third-party technology integrations tailored to your operational needs.
- Managed Detection & Notification: Swift alert triage, investigation, and notification of validated threats for seamless action.
- Security Platform Management: Comprehensive care from design to ongoing optimization, ensuring your security infrastructure is always at its best.
SIEM and SOC Integration
Tecplix offers a holistic and cost-effective cybersecurity solution by seamless integration of SIEM (Security Information and Event Management) technology and SOC (Security Operations Center) services, delivering a comprehensive defense approach with the following key benefits:
- Real-time Threat Detection and Response: By combining SIEM’s robust data analysis capabilities with our vigilant SOC team, we ensure that potential security threats are identified and addressed in real time, minimizing any potential damage.
- Proactive Security Measures: The synergy between SIEM and SOC allows us to take a proactive stance against cyber threats. This means identifying and mitigating potential breaches before they escalate, significantly reducing the risk of costly security incidents.
- Enhanced Regulatory Compliance: Our approach ensures that organizations meet regulatory compliance requirements effectively. Through detailed records and prompt responses to security incidents, we help maintain adherence to industry standards and data protection regulations.
- Optimized Operational Efficiency: SIEM technology and SOC services provide valuable insights into operational patterns. This enables organizations to make informed decisions, enhancing their overall security posture while also optimizing resource allocation for cybersecurity measures.
Ready to Enhance Your Security Posture?
Fill out this form and schedule a comprehensive assessment. Take the first step towards fortifying your defenses and securing your digital assets with confidence.


