In today’s rapidly evolving digital landscape, the ever-present threat of cyberattacks looms large over businesses of all sizes. Data breaches, malicious hackers, and advanced threats with evasive techniques pose substantial risks. Safeguarding your digital assets has never been more critical. In this context, the role of Vulnerability Assessment and Penetration Testing (VAPT) emerges as a powerful preventive tool, crucial for effective risk mitigation. This blog will help you explore the prowess of VAPT in helping secure your organization.
Role of VAPT in Enhancing Cybersecurity Posture
Vulnerability Assessment and Penetration Testing (VAPT) is a comprehensive security testing process designed to identify and rectify vulnerabilities in an organization’s IT infrastructure. It serves as the first line of defense against cyber threats, enabling organizations to stay ahead of potential breaches. VAPT consists of two main components, each with a unique role to play in shoring up your digital defenses:

Image 1: Vulnerability Assessment vs Penetration Testing
- Vulnerability Assessment: This initial phase systematically identifies, classifies, and evaluates vulnerabilities within your network, systems, and applications. These vulnerabilities can range from software weaknesses to configuration errors, potentially exploitable by cybercriminals.
- Penetration Testing: Ethical hackers or penetration testers simulate real-world attacks to exploit the vulnerabilities previously identified. The goal is to assess how well your organization can withstand these simulated threats and whether your defenses can hold up against determined attackers.
The Four Pillars of Vulnerability
The four primary categories of vulnerabilities that can potentially jeopardize your organization’s digital security.
- Software Vulnerabilities: Often tied to flaws or weaknesses in software applications, these can be exploited by hackers to gain unauthorized access or manipulate sensitive data. It is crucial to promptly address these vulnerabilities.
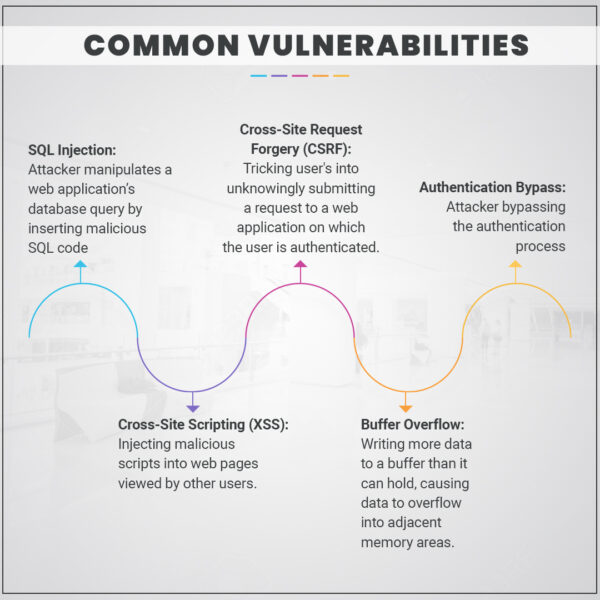
Image 2: Common Vulnerabilities
- Hardware Vulnerabilities: These weaknesses pertain to the physical components of your IT systems, including hardware devices, servers, or network equipment. Robust physical security measures are essential to mitigate these risks.
- Human Vulnerabilities: Human errors or negligence represent significant vulnerabilities. Phishing attacks, for instance, exploit human factors to trick individuals into revealing sensitive information or installing malicious software. Employee education and awareness are paramount.
- Configuration Vulnerabilities: Misconfigurations in software, systems, or networks can lead to vulnerabilities, inadvertently exposing sensitive data or providing unauthorized access. Regular audits and configuration management are vital in combating these vulnerabilities.
Vulnerabilities extend beyond IT systems to critical infrastructure. Protecting these essential systems becomes a matter of utmost priority, further underscoring the pivotal role of VAPT.
Distinguishing the Role of VAPT & Penetration Testing
While “VAPT” and “Pentest” are often used interchangeably, they possess distinct meanings:
- Vulnerability Assessment and Penetration Testing (VAPT): Encompassing both vulnerability assessment and penetration testing, VAPT provides a comprehensive view of your organization’s security posture, starting from identifying vulnerabilities to evaluating your organization’s defenses.
- Penetration Test (Pentest): Focuses solely on simulating cyberattacks to evaluate an organization’s security measures, aiming to identify vulnerabilities through controlled, real-world attack scenarios.
In essence, VAPT offers a more encompassing approach, providing a holistic view of your organization’s security posture.
Best Practices for Security Vulnerability Analysis
Conducting a robust security vulnerability analysis is a pivotal step in identifying and mitigating vulnerabilities effectively. Here’s a step-by-step guide on how to do it:
- Define Your Scope: Start by identifying the assets, systems, and networks that need assessment. Clearly defining the scope ensures that all relevant components are considered in the analysis.
- Vulnerability Scanning: Utilize specialized tools to conduct automated vulnerability scans. These tools can identify known vulnerabilities and misconfigurations in your systems and applications.
- Manual Assessment: Beyond automated scans, engage experts to manually assess your infrastructure. They can identify more complex or custom vulnerabilities that automated tools may miss.
- Prioritize Vulnerabilities: Not all vulnerabilities are equal. Implement a risk-based approach to prioritize vulnerabilities based on their potential impact and likelihood of exploitation.
- Remediation: Develop a plan to address and remediate the identified vulnerabilities. This may involve patching, reconfiguring systems, or implementing additional security controls.
- Reassessment: After remediation, conduct another round of testing to ensure that the vulnerabilities have been effectively addressed.
Protecting Critical Infrastructure
Protecting critical infrastructure is crucial, and VAPT plays a pivotal role in this endeavor. Here are additional steps to safeguard these essential systems:
- Continuous Monitoring: Implement 24/7 monitoring of critical infrastructure to detect and respond to security incidents in real-time.
- Access Control: Restrict access to critical systems and data to authorized personnel only. Implement robust authentication and authorization protocols.
- Security Awareness Training: Educate employees and personnel about cybersecurity trends and security best practices, including recognizing and reporting security threats.
- Redundancy: Build redundancy into critical systems to ensure continuity of operations, even in the face of cyberattacks or natural disasters.
- Collaboration: Work with government agencies, law enforcement, and other organizations to share threat intelligence and best practices for critical infrastructure protection.
- Regulatory Compliance: Stay up-to-date with relevant regulations and compliance requirements in your industry to ensure you meet all necessary standards.
Fortifying Your Digital Fortress
VAPT is not merely a buzzword but a fundamental component of a strong cybersecurity strategy. It serves as the shield that protects your organization from the relentless onslaught of cyber threats. By conducting a comprehensive security vulnerability analysis and implementing the right protective measures, organizations can successfully defend against cyber threats and safeguard their most critical systems.
Elevate Your Security Defenses with Tecplix’s VAPT Services
Tecplix recognizes the urgent need for a robust security posture and is dedicated to delivering solutions that fortify your digital assets. Our Vulnerability Assessment and Penetration Testing (VAPT) services uncover vulnerabilities within your systems and offer actionable insights to mitigate potential risks.
At Tecplix, our approach begins by understanding your distinct business context and pinpointing potential areas of vulnerability. Our team of certified security experts employs a blend of cutting-edge automated tools and manual testing techniques to unearth weaknesses within your systems.

Image 3: Tecplix VAPT Services
Tecplix goes beyond just identifying vulnerabilities; by offering detailed reports outlining each vulnerability, its potential ramifications, and recommended strategies for mitigation. We not only flag risks but also empower you with the knowledge required to proactively address them.
- Comprehensive Vulnerability Assessment: This entails automated scanning of systems to identify known vulnerabilities.
- In-Depth Penetration Testing: This simulates an attack on the system to unearth exploitable vulnerabilities.
- Risk Assessment: Every identified vulnerability is assessed based on its potential impact and the likelihood of exploitation.
- Reporting and Recommendations: A comprehensive report is provided, delineating each vulnerability, its potential consequences, and recommended strategies for mitigation.
- Re-Testing: Following the remediation of vulnerabilities, a re-test is conducted to ensure that the issues have been effectively addressed.
- Continuous Monitoring and Regular Audits: Security is an ongoing endeavor. Regular audits and continual monitoring are imperative to uphold a robust security posture.
What distinguishes Tecplix Apart
Tecplix’s VAPT services offer a steadfast solution to fortify your security posture. With its accomplished team, personalized approach, comprehensive reporting, and continuous support. Tecplix aids you in navigating the intricate landscape of cybersecurity, safeguarding your digital assets.
- Expert Team: Our team comprises certified security professionals with extensive experience in cybersecurity.
- Tailored Approach: Recognizing that every business is unique, we customize our VAPT services to align with your specific needs and business context.
- Comprehensive Reporting: We provide in-depth reports that not only spotlight vulnerabilities but also proffer actionable insights to alleviate these risks.
- Ongoing Support: Our commitment to clients doesn’t conclude with the delivery of the report. We offer continuous support to assist you in implementing the recommended security measures and fortifying your security posture over time.


