The digital revolution has provided endless opportunities, but it has also brought with it the constant threat of data breaches. As more and more organizations store sensitive information in the cloud, securing and maintaining its privacy becomes crucial. That’s where SOC 2 (System and Organization Controls 2) compliance comes in as one of the most recognized frameworks for cloud security.
What is SOC 2?
SOC 2 is a security framework developed by the American Institute of Certified Public Accountants (AICPA). This auditing standard is globally recognized and assesses an organization’s controls related to information security. It evaluates the effectiveness of the security controls that the service provider has implemented. During the audit, auditors review the service provider’s documentation, test the security controls, interview the staff, and observe the operations. The audit results in a report that can be either a Type I report, which covers the design of the security controls at a point in time, or a Type II report, which covers the design and operation of the security controls over a period of time. Organizations that undergo a SOC 2 audit demonstrate their commitment to data security and provide a level of assurance to customers, partners, and investors.
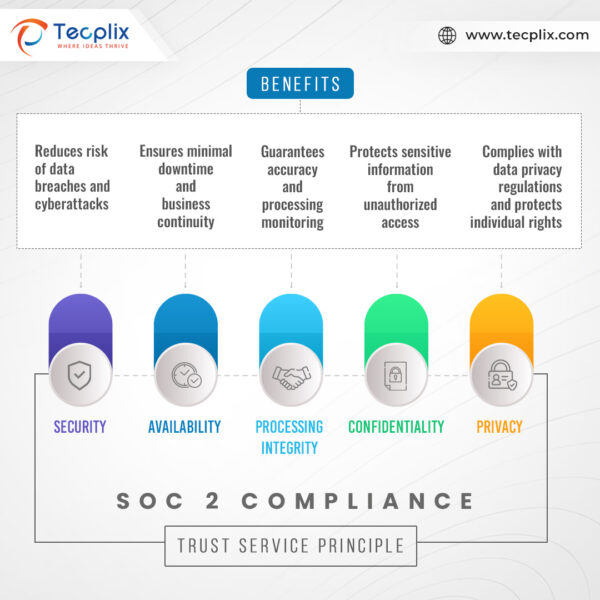
SOC 2 Principles and Benefits
The Five Trust Service Principles
- Security: This principle focuses on protecting systems and data from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes measures like access controls, encryption, and vulnerability management.
- Availability: It ensures that systems and data are accessible to authorized users when needed. This emphasizes measures like redundancy, disaster recovery planning, and uptime monitoring.
- Processing Integrity: It guarantees that systems process information accurately, completely, and timely by established procedures. This involves processes like data validation, backup and recovery procedures, and change management.
- Confidentiality: This principle emphasizes that sensitive information is only accessible to authorized individuals and is protected from unauthorized disclosure. This requires measures like data encryption, access control lists, and secure data disposal practices.
- Privacy: This principle focuses on the collection, use, retention, and disposal of personal data following established privacy policies and regulations. This includes obtaining informed consent, adhering to data minimization principles, and providing individuals with access to and control over their data.
The Benefits of SOC 2 Compliance
- Enhanced Data Security: It helps organizations identify and mitigate security risks, reducing the likelihood of data breaches and cyberattacks.
- Increased Customer Trust: SOC 2 compliance demonstrates a commitment to data security and privacy, fostering trust and confidence among customers, partners, and investors.
- Improved Regulatory Compliance: It helps organizations comply with various data privacy regulations, such as GDPR and HIPAA.
- Enhanced Competitive Advantage: In a competitive market, it offers a strong differentiator, attracting potential customers and partners seeking secure and reliable service providers.
- Reduced Costs: Implementing robust data security controls can help organizations avoid the significant financial implications associated with data breaches and regulatory fines.
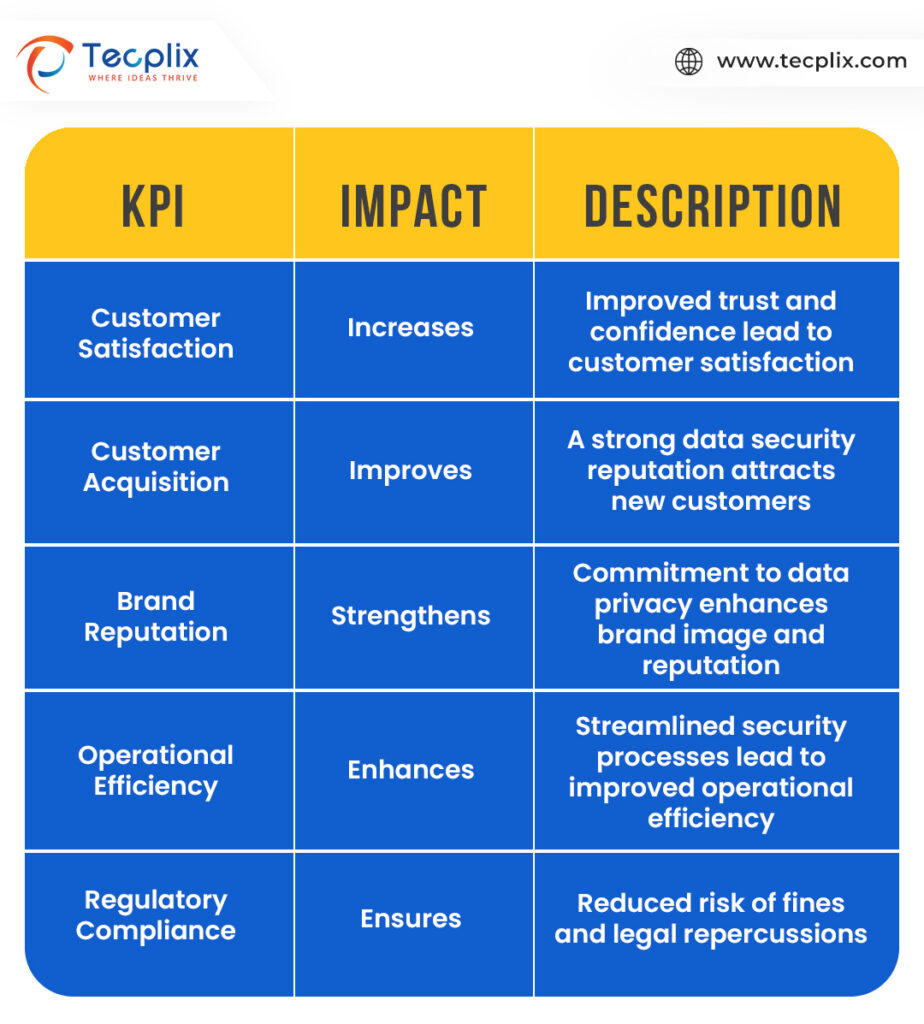
Impact on Key Performance Indicators
Achieving SOC 2 Compliance
Step 1: Selecting an Audit Firm:
Choose a qualified and independent audit firm with extensive experience in SOC 2 audits.
Step 2: Scoping and Risk Assessment:
Define the scope of the audit, including the specific systems and data in focus, and identify potential areas of risk.
Step 3: Testing of Controls:
The audit firm will conduct rigorous tests to evaluate the effectiveness of your organization’s controls in addressing the relevant trust service principles.
Step 4: Issuance of Report:
Upon successful completion of the audit, the audit firm issues a SOC 2 report detailing the scope, methodology, and findings.
Simplifying Your Journey
Several tools and resources are available to support organizations on their journey toward SOC 2 compliance:
- Interactive Tools: There are several tools that provide visually engaging and interactive exploration of the different aspects of compliance, facilitating a deeper understanding of the requirements and best practices.
- Case Studies: Learn from the experiences of organizations that have successfully achieved SOC 2 compliance, gaining valuable insights and practical guidance.
- Compliance Checklists: Utilize these checklists to assess your organization’s current level of compliance with SOC 2 standards, identifying areas for improvement and prioritizing action.
- Expert Support: Partnering with qualified professionals, such as audit firms and consultants, can provide invaluable expertise and support throughout the compliance process.
Securing Critical Data
In the current data-centric world, safeguarding sensitive information is crucial for businesses of any scale. SOC 2 compliance is a valuable structure that can aid in ensuring the safety of cloud-based data from unauthorized access, data breaches, and other potential security risks. By investing in SOC 2 compliance, service organizations can demonstrate their dedication to data security and establish trust with their customers.


