The convergence of people, processes, and technology has transformed our digital landscape significantly. AI and ML technologies are driving us forward, simplifying intricate and repetitive tasks to a great extent. This new era holds vast possibilities, but it has also revealed new horizons fraught with persistent and severe threats.
Within this evolving landscape, both organizations and threat actors highly prize personal data. Entities use personal information to enhance user interactions and improve their products. At the same time, malicious actors exploit this data for specific and harmful purposes, such as collecting ransom and disrupting operations.
Financial motives drive 95 percent of data breaches, marking a 24 percent increase since 2019. (Verizon)
What is Personal Data?
General Data Protection Regulation (GDPR)
According to the GDPR, personal information encompasses any data pertaining to a natural person who can be directly or indirectly identified. This identification can be established through various means, such as a name:
- identification number,
- location data,
- online identifier,
- Or specific factors related to the individual’s physical, physiological, genetic, mental, economic, cultural, or social identity.
Furthermore, the GDPR outlines “special categories” that cover sensitive information. These categories are subject to stricter regulations for the collection and processing of these data:
- race,
- ethnic origin,
- religious or philosophical beliefs,
- political opinions,
- trade union memberships,
- biometric and genetic data,
- health information, as well as data related to sexual preferences, sex life, and/or sexual orientation.
The California Consumer Privacy Act (CCPA)
Moving to the CCPA, personal data is defined as data that can identify, relate to, describe, or reasonably associate with a particular consumer or household. The CCPA extends protections to individuals and households but excludes certain information from the personal information category when publicly available, such as:
- data sourced from government records,
- professional licenses,
- and real estate records.
Digital Personal Data Protection Act (DPDPA)
DPDPA defines personal data as information identifying an individual or connected to that individual. It also specifies processing as automated or semi-automated operations performed on digital personal data, encompassing collection, storage, usage, and sharing.
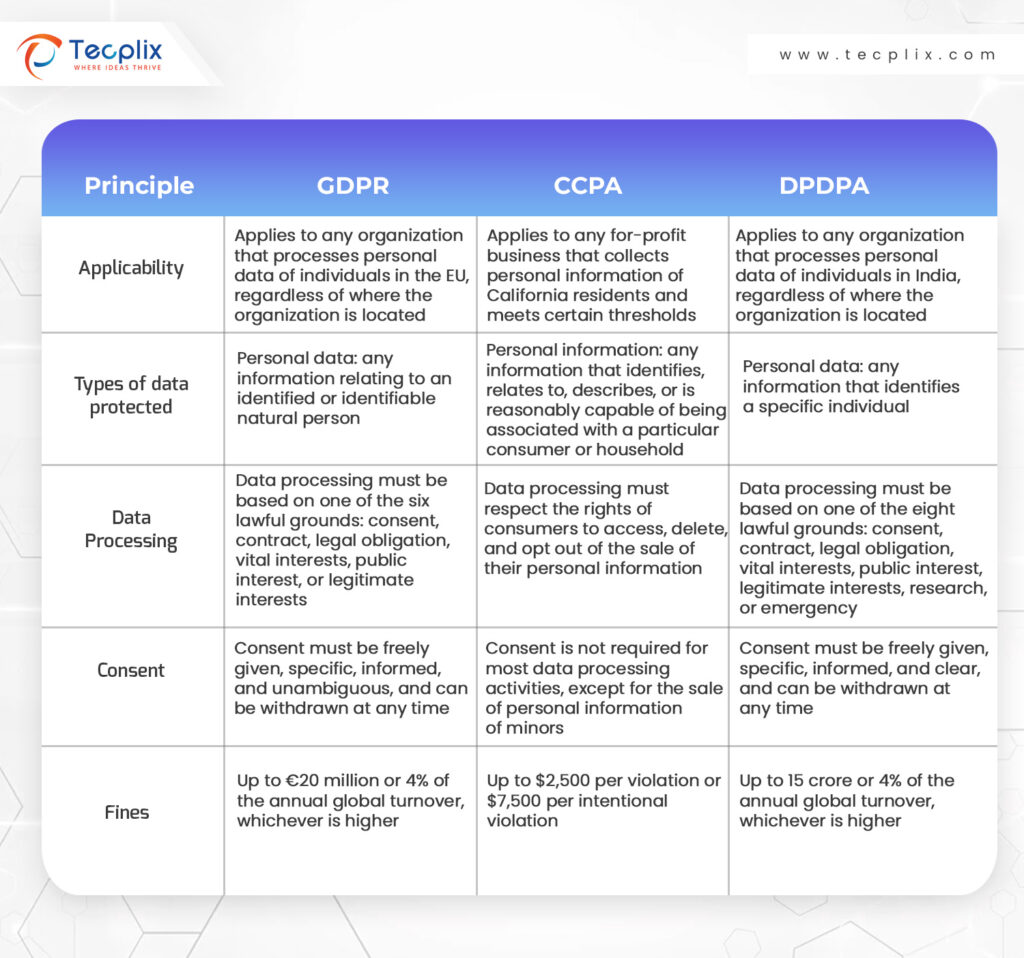
Figure 1: GDPR vs CCPA vs DPDPA
Classification of Personal Data
1. General Personal Data:
- Definition: Information that does not disclose specific personal characteristics.
- Examples: Name, email address, phone number, and date of birth.
- Sensitivity Level: Lower sensitivity; requires basic protection.
2. Sensitive Personal Data:
- Definition: Information revealing intimate aspects of identity.
- Examples: Racial/ethnic origin, political opinions, religious beliefs, health data.
- Sensitivity Level: Higher sensitivity; requires stringent protection due to potential risks.
Regulatory and Specialized Data Categories
3. PCI (Payment Card Industry) Data:
- Definition: Information used in payment card transactions.
- Examples: Card number, expiration date, security code.
- Regulation: Governed by PCI Data Security Standard (PCI-DSS).
4. NPI (Nonpublic Personal Information):
- Definition: Financial data collected by institutions.
- Examples: Account numbers, income, credit history.
- Regulation: Governed by the Gramm-Leach-Bliley Act (GLBA) to ensure privacy and security.
Specialized Protection Categories
5. PII (Personally Identifiable Information):
- Definition: Information used to identify an individual.
- Examples: Name, address, IP address, location data.
- Regulation: Requires specific protection due to identity theft and fraud risks.
6. PHI (Protected Health Information):
- Definition: Subset of PII focusing on health-related records.
- Examples: Medical records, lab reports, hospital bills.
- Regulation: Governed by the Health Insurance Portability and Accountability Act (HIPAA) within the healthcare sector.
Each classification carries distinct characteristics and varying levels of sensitivity, requiring tailored protection measures and compliance with relevant regulations to ensure privacy and prevent potential misuse or breaches.
For Users: Shielding Digital Identity
In today’s ever-expanding threat landscape, preserving personal information is paramount. Data theft threatens the very core of our privacy and financial security, jeopardizing sensitive details, from financial records to personal identifications. Cybercriminals relentlessly target these assets, aiming to exploit vulnerabilities and threaten individuals for financial profits.
Consequences of Breaches for Users
- Identity Fragmentation: Breaches pave the way for identity theft, fragmenting lives through financial turmoil and emotional distress.
- Financial Consequences: Unauthorized access to bank accounts or credit card details can lead to profound financial repercussions.
- Privacy Compromise: Personal data exposed in these breaches marks a profound incursion into one’s private life, shaking the very foundation of trust.
Attack Vectors to Lookout
- Phishing Attacks: Deceptive emails, texts, or messages impersonating trusted entities to deceive users into revealing sensitive information.
- Password Attacks: Exploiting weak or reused passwords to infiltrate personal accounts and extract valuable data.
- Malware Infestation: Infecting devices via compromised downloads, exposing vulnerabilities, and granting unauthorized access.
- Social Engineering Schemes: Manipulating human psychology to extract sensitive information or gain unauthorized access.
- Unsecured Wi-Fi Exploits: Intercepting data on public Wi-Fi networks, capitalizing on unsecured connections for data theft.
Fortifying Personal Defenses
- Phishing Awareness: Cultivate a cautious approach towards unsolicited emails or messages, verifying sources before divulging personal information.
- Password Security: Employ robust, unique passwords or passphrases across various accounts, refraining from password reuse.
- Safer Download Practices: Exercise caution when downloading files, ensuring legitimacy and verifying sources before installation.
- Awareness: Stay informed about social engineering tactics, fostering a critical eye toward unexpected requests for personal information.
- Secure Wi-Fi Usage: Prioritize secure Wi-Fi networks, utilize VPNs, and refrain from accessing sensitive data on unsecured connections.
- MFA: Employ Multi-factor authentication for all critical accounts.
For Organizations: Safeguarding Precious Data Vaults
For businesses, data theft looms as an ominous threat, jeopardizing financial stability, brand integrity, and operational continuity. It encompasses the illicit acquisition of sensitive company data, customer records, and trade secrets, bearing far-reaching consequences that resonate throughout the organization.
Consequences of Breaches for Organizations
- Financial Consequences: Breaches trigger financial crises, entangling businesses in recovery expenses, legal battles, and regulatory fines.
- Reputation’s Precarious Stand: Trust erodes, precipitating customer exodus and shattering the meticulously crafted image of reliability.
- Operational Quandaries: Downtime during recovery becomes a haunting reality, disrupting operations and threatening business continuity.
- Legal Minefields: Violation of data protection regulations unveils a minefield of legal ramifications, further exacerbating the aftermath.
Attack Vectors for Organizations
- Phishing and Social Engineering: Targeting employees through deceptive communication to extract sensitive data or infiltrate systems.
- Insider Threats: Malicious actions or negligence from insiders, including employees or contractors, leading to data breaches.
- Vulnerability Exploitation: Capitalizing on system weaknesses, software bugs, or unpatched systems to infiltrate organizational networks.
- Malware Intrusions: Deploying malware to infiltrate systems, granting unauthorized access, or compromising data integrity.
- Physical Intrusions: Theft or unauthorized access to physical devices or documents containing sensitive information.
Defensive Measures for Organizations
- Comprehensive Employee Training: Educate employees on identifying phishing attempts and the importance of data security.
- Robust System Patching: Implement regular updates and patching to fortify systems against vulnerabilities and malware threats.
- Access Control Measures: Enforce stringent access controls, limiting data access based on job roles and responsibilities.
- Incident Response Protocols: Develop and regularly test incident response plans to mitigate the impact of potential breaches.
- Physical Security Measures: Implement physical security protocols to protect against theft or unauthorized access to devices and documents.
- MSSP Partnership: Organizations can ensure a resilient security posture by partnering with the right Managed Security Services Provider.
Other Important Regulations:
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA regulates the protection and handling of sensitive health information (Protected Health Information – PHI) in the healthcare industry. It mandates security standards to protect individuals’ medical records and other personal health information.
- Payment Card Industry Data Security Standard (PCI DSS): This applies to businesses that handle credit card information. It outlines security standards to ensure the safe handling of sensitive cardholder data to reduce credit card fraud.
- Personal Information Protection and Electronic Documents Act (PIPEDA): Canadian federal law governing how private sector organizations should collect, use, and disclose personal information during commercial activities. It establishes rules for obtaining consent and safeguarding data.
- Children’s Online Privacy Protection Act (COPPA): COPPA applies to the online collection of personal information from children under 13 years of age in the United States. It requires verifiable parental consent and imposes restrictions on the handling of children’s data.
Proactive Vigilance, Protected Future
Understanding the diverse attack vectors and the severe consequences of data theft is pivotal. Both users and organizations must not only fortify their defenses but also remain vigilant against these multifaceted threats. Individuals and organizations can navigate the digital world with resilience by comprehending the intricacies of attack vectors, understanding the dire consequences, and fortifying defenses through proactive measures.
More Related Articles:


