Security Information and Event Management (SIEM) systems generate numerous alerts daily, making it difficult for security teams to identify genuine threats promptly. The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework bridges this gap, offering a structured way to transform SIEM alerts into actionable insights. This blog provides a step-by-step approach to mapping SIEM alerts to MITRE ATT&CK and explains its benefits for enhancing threat detection and incident response.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK framework is a globally recognized knowledge base of adversary tactics, techniques, and procedures (TTPs). It provides a standardized taxonomy that helps organizations effectively understand and respond to cybersecurity threats.
Core Components of the Framework
- Tactics: High-level objectives attackers aim to achieve (e.g., Initial Access, Persistence).
- Techniques: Methods used to accomplish tactics (e.g., Credential Dumping).
- Sub-techniques: Specific approaches under a technique (e.g., NTDS Dumping under Credential Dumping).
- Integrating SIEM alerts with this framework helps security teams gain deeper insights into potential attack patterns and respond effectively.
Why Map SIEM Alerts to MITRE ATT&CK?
- Improved Contextualization: Mapping SIEM alerts to ATT&CK techniques connects isolated events to broader attack patterns, providing a more precise context for potential threats.
- Comprehensive Threat Detection: The ATT&CK framework ensures complete coverage of all adversary tactics and techniques, helping identify gaps in detection rules and enhancing overall visibility.
- Streamlined Incident Response: Categorizing alerts by ATT&CK techniques enables security teams to prioritize high-impact threats, accelerating response times.
- Proactive Threat Hunting: By analyzing mapped alerts, security teams can anticipate adversary movements and implement preventive measures before an attack escalates.
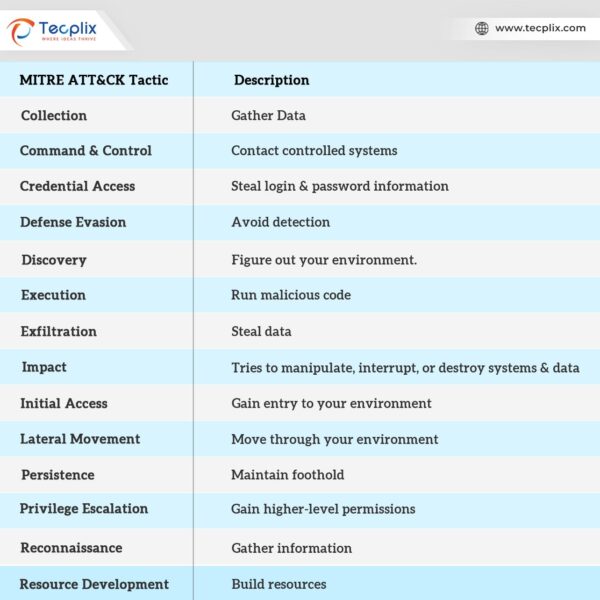
MITRE ATT&CK TACTICS
How to Map SIEM Alerts to MITRE ATT&CK: Step-by-Step
Step 1: Identify Relevant SIEM Alerts
- Filter SIEM alerts to focus on events with security implications.
- Remove routine system activities to avoid false positives.
Example:
- Alert: Repeated failed login attempts followed by success.
- Mapped Tactic: Credential Access.
- Mapped Technique: Brute Force (T1110).
Step 2: Map Alerts to ATT&CK Tactics
- Categorize each alert by its associated ATT&CK tactic, such as Initial Access, Execution, or Exfiltration.
- Use the official MITRE ATT&CK framework as a reference.
Example:
- Alert: Unusual data transfer to an external IP.
- Mapped Tactic: Exfiltration.
- Mapped Technique: Data Exfiltration Over Unencrypted Channels (T1048).
Step 3: Map Alerts to Techniques and Sub-techniques
- Analyze alert details (log source, timestamp, and event description) to identify specific techniques and sub-techniques.
Example:
- Alert: Phishing email with a malicious attachment.
- Mapped Tactic: Initial Access.
- Mapped Technique: Phishing (T1566).
- Mapped Sub-technique: Spear Phishing Attachment (T1566.001).
Step 4: Analyze and Prioritize Alerts
- Group alerts to identify patterns, such as coordinated attacks or lateral movement.
- Prioritize alerts based on their severity, potential impact, and likelihood of exploitation.
Step 5: Integrate with Incident Response
- Embed mapped alerts into your incident response workflow.
- Use the MITRE ATT&CK framework to refine detection rules and enhance threat-hunting processes.

MITRE ATT&CK FRAMEWORK
Real-World Use Cases
Detecting Spear Phishing
- Alert: Malicious email detected.
- Mapped Tactic: Initial Access.
- Mapped Technique: Phishing (T1566).
Identifying Lateral Movement
- Alert: Unauthorized Remote Desktop Protocol (RDP) connection.
- Mapped Tactic: Lateral Movement.
- Mapped Technique: Remote Desktop Protocol (T1021).
Responding to Malware Execution
- Alert: Suspicious file executions on multiple systems.
- Mapped Tactic: Execution.
- Mapped Technique: Malicious File (T1204).
Benefits of MITRE ATT&CK Integration
- Improved Threat Visibility: Understand attacker tactics and techniques in context.
- Enhanced Defense Strategies: Identify and address gaps in detection and response.
- Faster Incident Resolution: Prioritize and respond to high-impact alerts quickly.
- Proactive Cybersecurity: Stay ahead of adversaries with a structured approach.
Conclusion
Mapping SIEM alerts to the MITRE ATT&CK framework empowers organizations to bridge the gap between raw data and actionable threat intelligence. By contextualizing alerts, identifying detection gaps, and streamlining incident response, security teams can build a proactive defense against sophisticated adversaries. This integration provides a robust, proactive approach to cybersecurity, enabling security teams to effectively detect, respond, and prevent sophisticated cyber threats.


