Imagine receiving an urgent email from your bank, alerting you to a suspicious transaction on your account and prompting you to click a link to resolve the issue immediately. Or picture receiving a seemingly innocent message from a trusted colleague asking for confidential information. These scenarios are common examples of a dangerous cyber threat that plagues the digital world—phishing.
Phishing is a malicious technique employed by cybercriminals to deceive individuals into divulging sensitive and personal information, such as passwords, credit card numbers, or social security numbers. Typically, it involves impersonating trusted entities or individuals through fake emails, websites, messages (smishing), or calls (vishing) that appear legitimate at first glance. The ultimate goal of phishing is to trick the recipient into compromising their security and privacy, making it a potent weapon in the arsenal of online fraudsters.
Phishing has evolved significantly over the years. It has progressed from simple emails laced with poor grammar containing malicious links or attachments to sophisticated phishing kits available on the dark web. Techniques now include conversation hijacking, phishing emails with embedded QR codes, and captchas. Another critical aspect of phishing is that it often serves as the initial attack vector in high-profile breaches and compromises.
In this three-part phishing email analysis series, we will explore effective ways to analyze phishing emails. These insights will be valuable not only for cybersecurity professionals but also for the general public, regardless of their work roles. Essentially, anyone with an investigative mindset will find this series appealing.
Types of Phishing Email Analysis
There are two broad techniques for analyzing phishing emails:
- Static Analysis
- Dynamic Analysis
Static Analysis
Static analysis of a phishing email involves examining the email without executing its contents. Analysts review various attributes such as sender information, email content, links, and attachments to identify potential signs of phishing. By scrutinizing these elements, security professionals can assess the legitimacy of the email and determine if it poses a threat, without actively engaging with potentially malicious content. Email static analysis can be classified into two types:
- Email Body Analysis
- Email Header Analysis
In Part 1 of this series, we will explore the various aspects of the email body analysis technique.
What is Email Body Analysis?
- Sender Email Address: Phishing emails often use addresses that mimic legitimate ones but may have subtle misspellings or extra characters. An email from a personal address (e.g., gmail.com, yahoo.com) claiming to be from an organization is also likely from a phishing actor.
- Generic Greetings: Phishing emails often use generic greetings like “Dear Customer,” “Hi,” or “Hello” instead of addressing you by name. Legitimate organizations usually personalize their emails.
- Urgent or Threatening Language: Phishing emails frequently create a sense of urgency or use threatening language to prompt quick action. They may claim that your account will be suspended unless you act immediately.
- Emails from Co-workers/CEOs: Emails from co-workers asking for confidential information or ones from CEOs requesting large sums of money to be transferred to their personal accounts are common phishing tactics that have caused significant financial losses and reputational damage to companies worldwide.
- Gift Lures/Shipment Emails: Phishing emails may entice recipients with promises of free gifts or prizes, luring them into clicking on malicious links or providing personal information. Legitimate organizations typically do not randomly give away gifts via email. Shipment emails (e.g., DHL, FedEx) asking you to click a link to provide personal and payment information are also common phishing tactics.
- Spelling and Grammar Errors: Phishing emails might contain spelling and grammar mistakes, though this indicator is becoming less common with the emergence of generative AI technology.
- Fraudulent Email Attachments: Various patterns are seen in phishing email attachments, such as invoices for items or services you never purchased. Recently, QR codes have also been used as attachments, allowing threat actors to embed malicious links within QR codes and bypass spam filters. Another tactic is sending an attachment that appears to be a PDF but is actually an image with embedded links. When the image is clicked, the victim is redirected to a malicious website aimed at capturing their credentials.
Email Body Analysis Tools
Now, let’s explore some powerful tools that can be used to effectively analyze an email body.
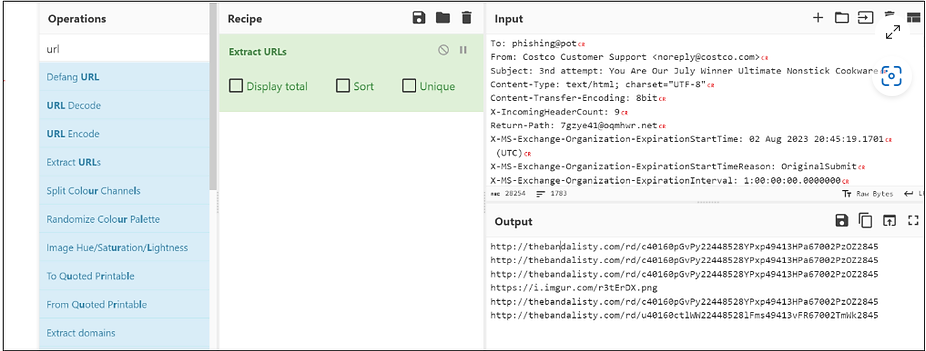
- CyberChef: CyberChef is a versatile tool with numerous features essential for a SOC Analyst’s toolbox. It can encode, decode, format data, parse data, encrypt, decrypt, compress, extract data, defang URLs, and more. For email body analysis, the “Extract URLs” feature is particularly handy. It helps identify various URLs embedded in the email body.
- How to Use CyberChef:
- Go to the CyberChef web app.
- From the “Operations” section, select “Extract URLs” and drag it to the “Recipe” section.
- Copy the text from the email source (raw HTML data containing the email header and body) and paste it into the “Input” section.
- Click on “BAKE!” to view the output, which will show all the extracted URLs.
- How to Use CyberChef:
Source: CyberChef
-
-
- The “Extract domains” operation can also be used to extract all domains from the email body.
-
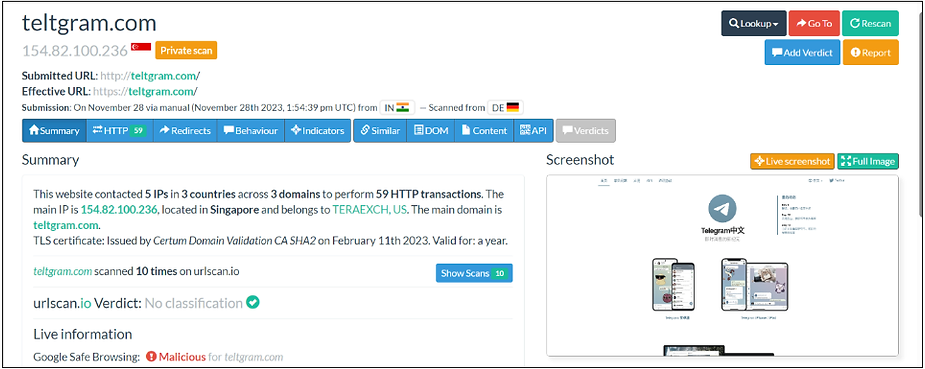
- URLscan.io: URLscan.io is a free service for scanning and analyzing websites. When a URL is submitted, the automated process browses to the URL like a regular user, recording the activity the page navigation creates. This includes domains and IPs contacted, resources requested from those domains, and additional information about the page itself.
- How to Use URLscan.io:
- Go to URLscan.io and paste the suspicious URL.
- Select the preferred “Visibility” option (Public/Unlisted/Private).
- How to Use URLscan.io:
Start the scan. URLscan.io will browse to the URL internally, provide a screenshot of the malicious website, and display further details such as IPs contacted, IP locations, and DNS information.
Source: urlscan.io
- VirusTotal/Cisco Talos/AbuseIPDB: These are popular tools for domain, URL, and IP checks. Information obtained from the tools mentioned earlier can be checked on these reputation websites for a detailed analysis. The reputation of an email attachment can also be analyzed by calculating its hash value and checking it on VirusTotal or Cisco Talos.
Sample Analysis 1
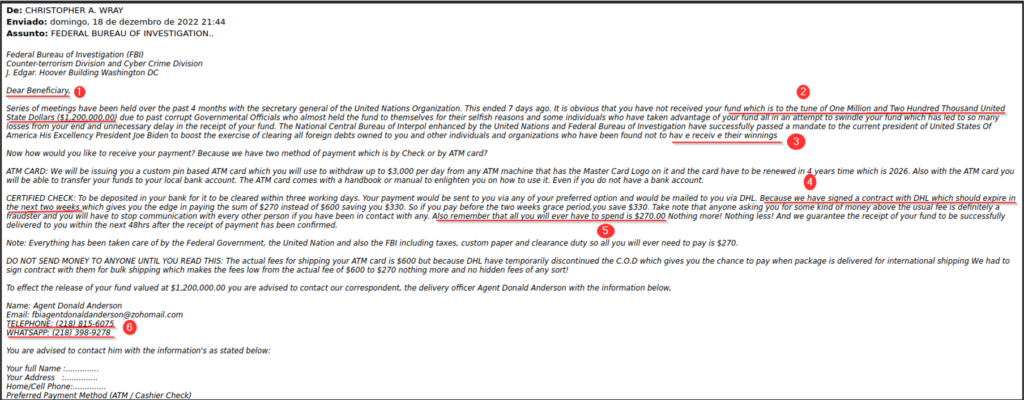
Let’s analyze a sample email body from a suspicious phishing email.
The email pretends to come from the FBI and discusses an “imaginary” fund the recipient is entitled to. Let’s go through the indicators one by one:
- The email starts with a generic greeting, “Dear Beneficiary,” a common method seen in mass phishing campaigns targeting a large number of people.
- The email uses a gift lure, offering $1,200,000 to entice the user. (Logic often doesn’t apply when free money is involved!)
- The email contains spelling and grammatical errors.
- The email creates urgency by mentioning that the contract with DHL will expire in two weeks.
- The email asks for money to receive the shipment, a very common phishing indicator.
- The email provides a telephone and WhatsApp number for the user to call back. This is a phishing method known as Telephone Oriented Attack Delivery (TOAD), where the email may not contain a malicious link or attachment but instead creates fear or urgency to prompt the victim to call the attacker’s contact number. Through the phone call, the attacker compromises the user by obtaining their credentials, forcing them to pay, or installing malware on their device.
From these indicators, it’s clear that the email has nothing to do with the FBI.
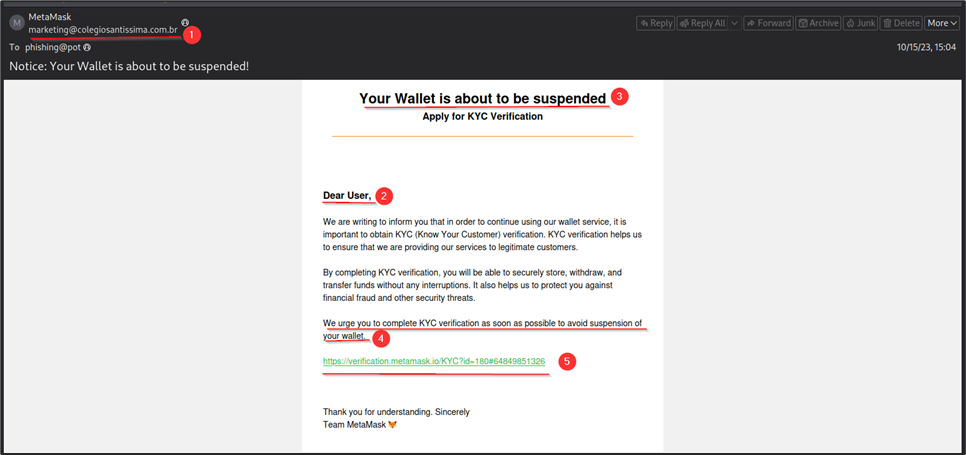
Sample Analysis 2
Now, let’s analyze another suspicious phishing email that pretends to come from MetaMask and asks the recipient to complete KYC to avoid suspension of their cryptocurrency wallet.
- The sender’s email address is suspicious and not from MetaMask; it is from a different domain.
- The email uses a generic greeting, “Dear User.”
- The email creates fear and urgency by claiming that the user’s wallet is about to be suspended, prompting immediate KYC verification. This is a fraudulent attempt to gain the victim’s confidential information.
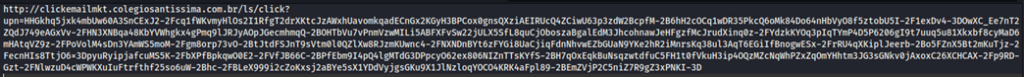
- A URL is mentioned that seems to come from MetaMask’s official website. However, hovering over the link reveals that it is not the original link where the user will be redirected. (Hovering may not always work as intended, especially when URL shortening is employed.) The original link can also be obtained from the HTML source of the email.
- The original link observed is suspicious.
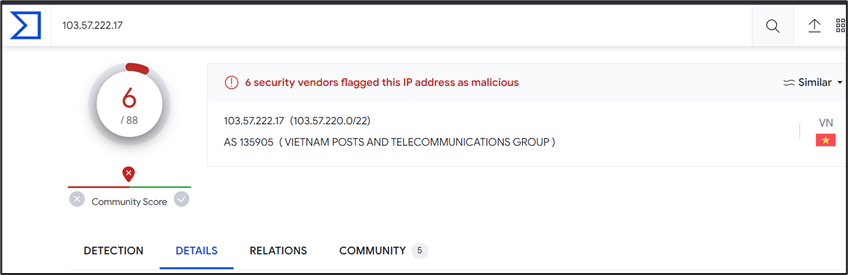
On analyzing it with URLscan.io, more details are uncovered.
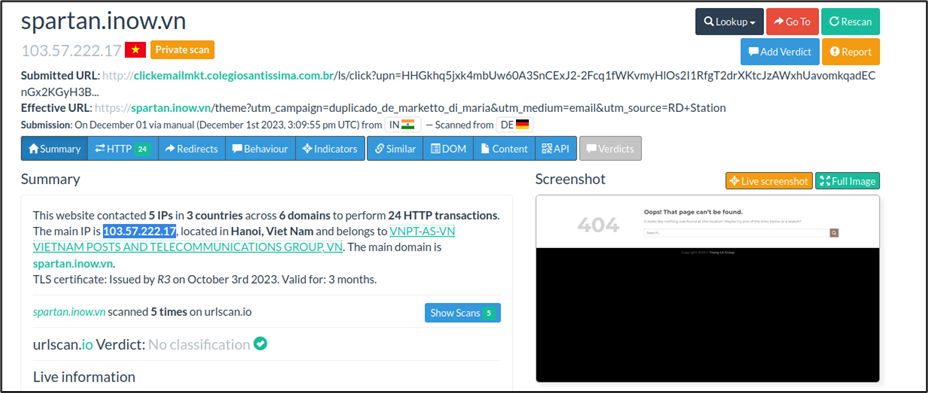
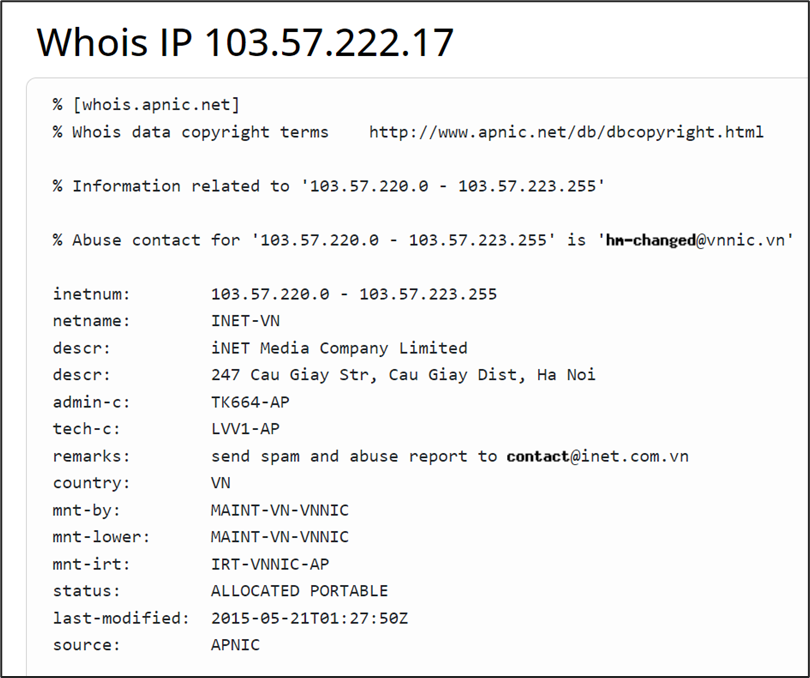
Not much details are available regarding the domain but the related IP 103[.]57[.]222[.]17 is flagged as malicious by VirusTotal. The IP is located in Hanoi, Vietnam and belongs to “iNET Media Company Limited” according to WhoIs details.
Moving Ahead
Phishing remains a significant cyber threat with ever-evolving tactics aimed at deceiving recipients. By using static analysis techniques, such as email body analysis, you can spot numerous indicators that reveal the malicious intent behind phishing emails. Tools like CyberChef, URLscan.io, VirusTotal, and Cisco Talos are invaluable in these efforts, providing detailed insights into the URLs, domains, and IPs associated with suspicious emails.
In Part 2 of this series, we will dive deeper into email header analysis, exploring how to uncover hidden details that can confirm the legitimacy—or lack thereof—of an email. Stay tuned for a comprehensive guide that will further equip you with the skills to tackle phishing emails head-on.
“The three-part phishing email analysis series, we will explore effective ways to analyze phishing emails.
This series is fully practical and analyzes real phishing samples collected via honeypots (credits: Phishing Pot Project)”
Author:
Anand R. Menon
SOC Lead- Tecplix